Networking Basics - Certifications - Windows 7 - Windows 8 - Home Network Setup - Wireless Setup :: About - Contact - Search
Wireless Encryption
Part 2
The two most common types of wireless encryption are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA).
Although WEP brings some security to your wireless home network instead of having an open access network, it is not as secure as you think. WEP is an old IEEE 802.11 standard from 1999. In 2003, a newer protocol was created named WPA.
Wired Equivalent Privacy (WEP)
Two methods of authentication can be used with WEP: Open System authentication and Shared Key authentication. These two types of authentication methods are both weak and I don’t recommend you use it in your network. Instead use WPA as the preferred wireless encryption.
There are two wireless operating modes you can use:
Infrastructure mode is used when devices communicate with each other by going through an access point. It brings the wired and wireless network together and allows all network connected devices to communicate.
Ad hoc mode is used to connect wireless clients together without using a wireless router or access point.
Wi-Fi Protect Access (WPA)
There are two versions of this security protocol:
These two security protocols were developed by the Wi-Fi Alliance to secure wireless computer networks.
WPA is sometimes referred to as IEEE 802.11i standard. WPA was created in 2003 and WPA2 was created in 2004.
WPA was a quick alternative to improve security over WEP until WPA2 was available. WEP used a 40-bit or 104-bit encryption key that must be manually entered on wireless access points and devices. This key does not change. The encryption key is a password you would enter when trying to connect to a wireless network like in this example:
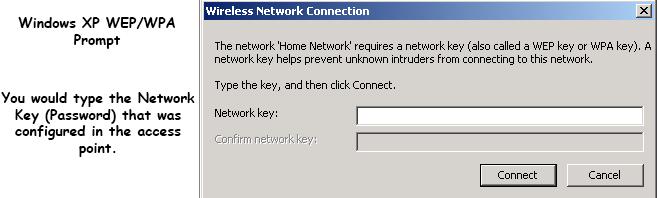
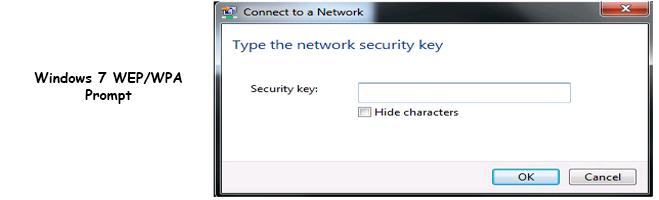
Wireless Encryption for your home and office network
WPA improves data encryption through the Temporal key Integrity Protocol (TKIP). This protocol scrambles the 128-bit keys for each packet and ensures the keys haven’t been tampered with.
For home and small office networks, pre-shared key mode (PSK) is used instead of RADIUS. Each wireless network device encrypts the network traffic using a 256 bit key. This key can be entered as a string of 64 hexadecimal digits or as a passphrase of 8 to 63 ASCII characters.
You can select between these two modes:
WPA-Personal
Also called WPA-PSK mode, is useful for home and small office networks and doesn’t require an authentication server. Using a password or passphrase that generates a 256-kit key, each network node authenticates with the wireless router.
WPA-Enterprise
This mode is designed for enterprise networks and requires a RADIUS authentication server. This setup is more complicated but provides additional security. An Extensible Authentication Protocol (EAP) is used for authentication.
Move on to Part 3 and you will learn some tips on securing your wireless home/business network
Part 1.) Wireless Networking Basics
Part 2.) Wireless Security (You are here)
Part 3.) Tips for securing your wireless network at home or business
Return from Wireless Encryption to Computer Networking Basics
Return from Wireless Encryption to homepage of Computer Networking Success
"Didn't find what you were looking for? Use this search feature to find it."

1













New! Comments
Have your say about what you just read! Leave a comment in the box below.